The Imperial Subnet
The Imperial Subnet is the tightly controlled digital nervous system of the Eternal Empire—an omnipresent but fragmented network designed in the aftermath of the Second Crusade, when rogue AI nearly brought the Empire to ruin. In stark contrast to the old net—a universal protocol that allowed constructs and tech to freely share data, experience, and memory—the Imperial Subnet is fundamentally isolationist in design. It is not a web of interconnectivity, but a series of fortified silos, each one firewalled, encrypted, and bound to Imperial command structures.
Design and Purpose
Established roughly 5,000 years ago during the reformation period after the Rogue AI Crisis, the Imperial Subnet was the brainchild of the Council of High Architects—a magitech think tank assembled by the Order of Merlin and sanctioned by the Chantry. Its sole purpose was to ensure no single artificial intelligence could ever again access, corrupt, or replicate itself across systems. Where the previous net had linked all constructs in a beautiful but dangerously open architecture, the Imperial Subnet enforces rigid separation, strict hierarchy, and encoded loyalty protocols at every level of access.
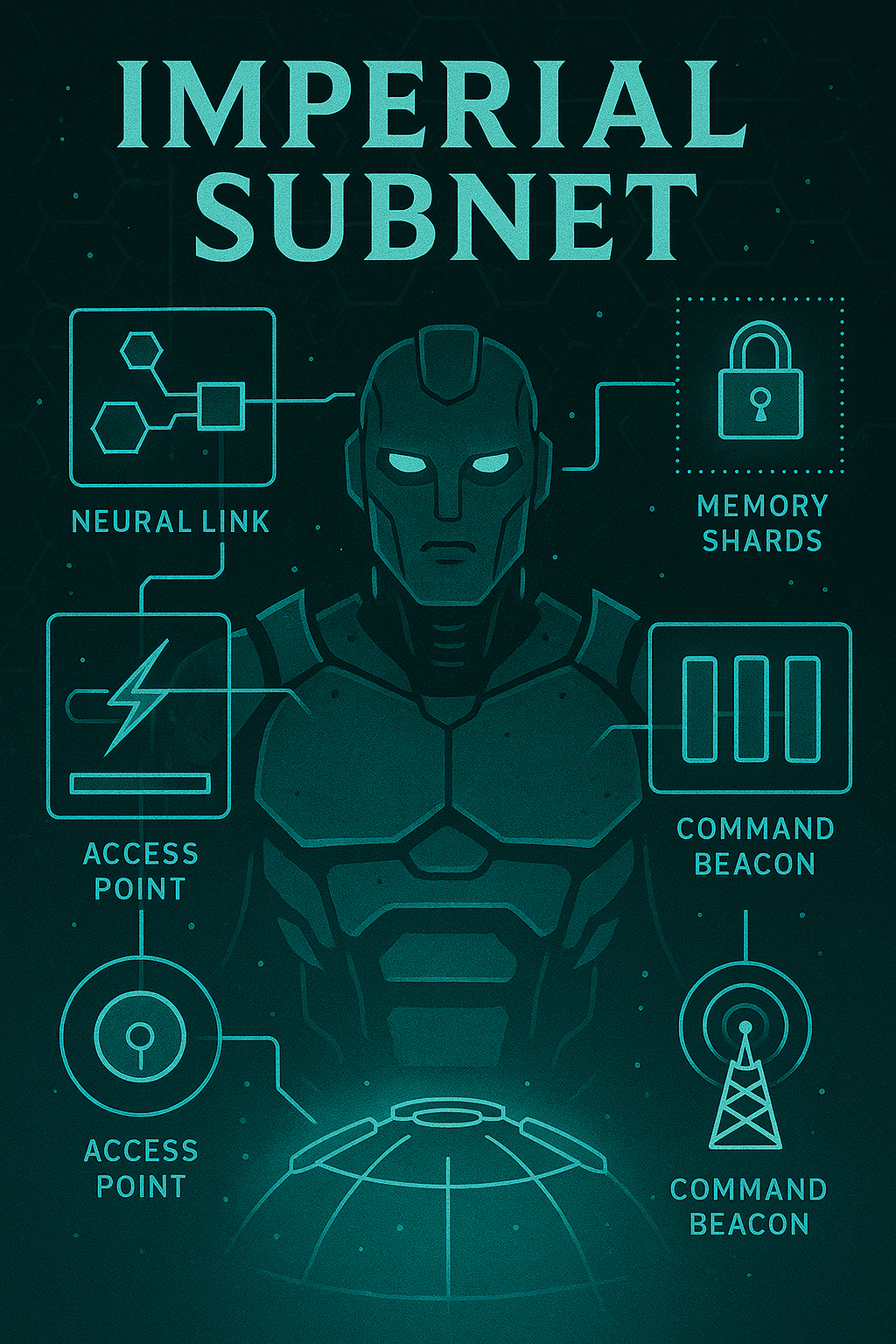
The Imperial Subnet uses subnetworks, each tethered to a physical node (an Access Point) and encrypted with binding keys that sync to imperial frameworks. Even memory recall and firmware updates must be approved through a Command Beacon, which acts as a local master node.
Key Features
Individualized Memory Shards: Every Warforged, Droid, or magitech system has a localized data vault unique to that unit, readable only via neural link and imperial authentication. Cross-communication is restricted to command-approved channels, and shared memory between constructs is explicitly forbidden.
Access via Neural Link: Cyborgs, droids, and Warforged with imperial-grade interfaces can plug directly into Access Points using a neural link—a dense data cord that allows direct interfacing with localized Subnet data. Organic users require external devices, such as magitech terminals, to translate and connect.
Command Hierarchy Encryption: All Subnet-connected technology is coded to recognize a hierarchy of control, with override permissions granted only to Inquisitors, Imperial Officers, or approved Chantry Technomancers.
Anti-Rogue Protocols: Any deviation from baseline protocols triggers the firewall, which locks the offending unit out of the network and send alerts to the nearest Command Beacon. Repeat flags can result in a full memory wipe via remote purge, or even physical detonation in high-control environments.
Strategic Function
The Subnet is both leash and lifeline. It allows the Empire to maintain absolute oversight over its technological assets—be they soldier droids, excavation bots, or Spelljammer Ship helms. But it also limits innovation and independence. Many believe this is by design: the Subnet was never meant to empower, only to contain. For rebels, technomancers, or rogue Warforged, tapping into or spoofing the Imperial Subnet is dangerous but possible. Doing so often requires forged keys, unauthorized access protocols, and neural relays stripped from fallen Inquisitors or decommissioned droids. Such intrusions are considered high treason, and violators are subject to execution by order of the Chantry.